Onward...to pwn GOAD!
We got DA on GOAD SCCM, so let's attack the original
Hi friends! In this newsletter:
ICYMI: we pwned GOAD SCCM!
A few gotchas when installing GOAD (Game of Active Directory)
Tales of pentest pwnage with a side order of Shadow Credentials sauce
ICYMI: we pwned GOAD SCCM!
We recently completed a two-part series (here’s part 1, here’s part 2) on hacking GOAD SCCM, which is an absolutely fabulous lab packed with the common issues/vulnerabilities found in Microsoft SCCM. As a reminder - these episodes have video as well - which you can grab on our YouTube channel or livestream schedule.
Our pal Joe “The Machine” Skeen joined us for both episodes, and we worked our way through:
Attacking SCCM with no creds
Relaying the machine account of the MECM box over to the SQL server to get local admin
Using smbclient-ng to pilfer through boxes via relayed credentials
Extracting encrypted credentials from the SQL component of SCCM
Decrypting DA creds on the main SCCM box
It was an absolutely jolly good time. Have you figured out other ways to pwn GOAD SCCM?
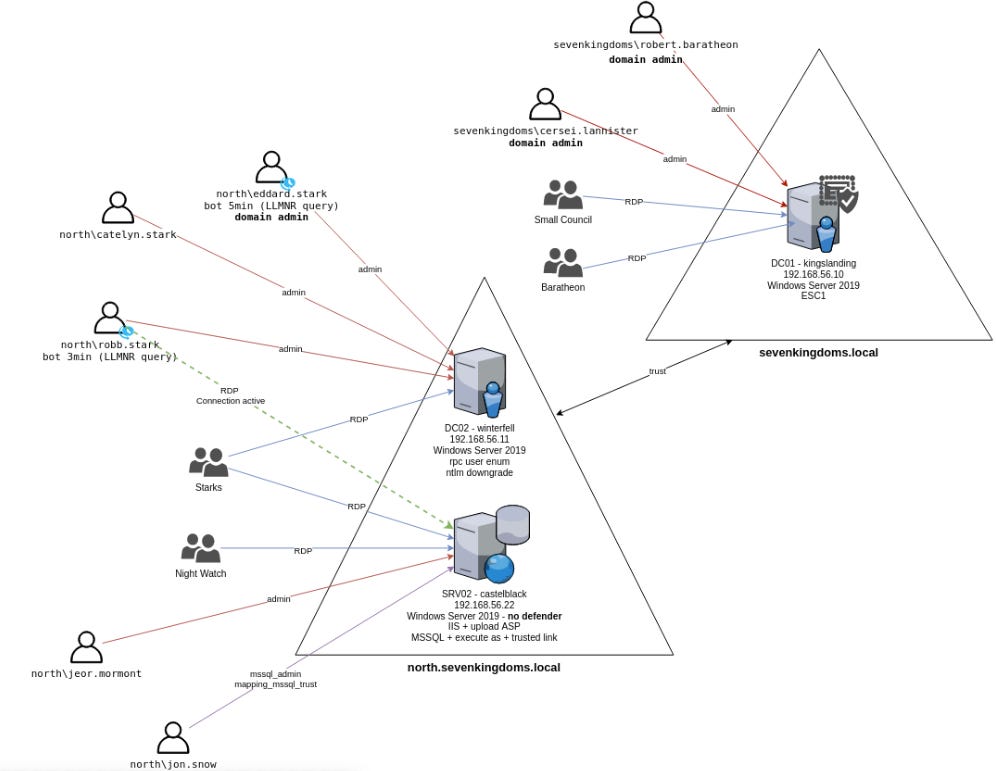
Now onward to pwn GOAD!
After having so much fun with SCCM, the next few livestreams will (almost certainly) be focused on the original flavor of GOAD. Thanks to the magic of Ludus.cloud (which I talked about in this episode and this episode), I was able to tear down my GOAD SCCM lab and pop up the fresh GOAD lab in just a few commands.
I did run into one snag though. The install bombed out right at the end with some weird error: Something wrong during the provisioning task : ad-relations.yml. I opened an issue about it, and while I was doing additional troubleshooting, I read through some of the recently closed issues. Many of them had common resolutions: try the install again, wait a while and then try the install again, or give all the DCs a bounce and try the install again.
Third option was the charm for me. I brought each DC down, then booted them up, one by one, with about 5 minutes delay in between (just to give pleeeeenty of time for the DCs to finish updates and settle). When I tried the install again, BOOM, it finished perfectly. I then shut everything down, gave it a snapshot, and will start hacking away at it later this week. I mean, just look at this place…it’s beautiful!
Tales of pentest pwnage with a side order of Shadow Credentials sauce
Coming up on Friday’s podcast, I’ve got a really fun tale of pentest pwnage for you that involves the Shadow Credentials attack. If you’re not familiar with that attack, this video does an awesome job of showing/explaining it:
Have a wonderful rest of your week, and if you’re in the market for a pentest, controls assessment or training session, give us a shout - either at 7MinSec.com or just leave a DM here:
Thanks!
Brian