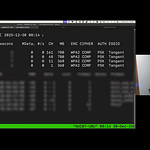
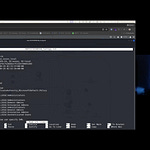
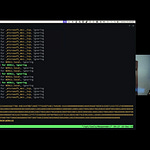
In this week’s Tuesday TOOLSday, we showed how you could run BloodHound with a machine account credential and start doing some intense domain enumeration. Normally on an assume compromise pentest I’d just use my low-priv account to do this, but remember that with Ninja Hacker Academy, you start with no cred, so getting a machine account cred is a pot of gold! I also showed how you can use bloodhoundcli to very quickly mount BloodHound data and start sifting through it.
Don’t forget we did a NHA deep-dive yesterday as part of our third Thursday YouTube series - details at https://7minsec.com/live.
-Brian